Why Mastering Database Design for Backend Development is Crucial
Last update: 21 December 2023 at 09:49 am
If you’re a backend developer, you know that a database design is the backbone of any successful application. It’s the heart that stores retrieves, and manipulates data.
Introduction:
However, not all database designs are created equal. In this blog post, we’ll take a closer look at the importance of database design and how to do it right.
Are you tired of dealing with slow and unreliable databases for your back-end applications? Look no further! We will dive into the world of database design and uncover the secrets to creating a seamless and efficient database management system for storing, retrieving, and manipulating data.
From the importance of normalization to the power of denormalization, we’ve got you covered on all things database design. So sit back, relax, and let’s get started on building the backbone of your next successful application.
Why Database Design Matters
As the amount of data being stored continues to grow, the importance of proper database design becomes more apparent.
A well-designed database can greatly improve the performance and scalability of an application. In fact, according to a study by Gartner, poor database design can lead to a 30% reduction in application performance.
Are you looking for a backend agency?
Discover the most relevant agencies for your project based on your own specific requirements.
Find an agency!The Importance of Normalization
One of the most important concepts in database design is normalization. This is the process of organizing data into separate tables to reduce data redundancy and improve data integrity.
For example, instead of storing all customer information in one table, it would be better to split it into separate tables for customer details, contact information, and purchase history.
Normalization can also help improve query performance by reducing the amount of data that needs to be scanned. According to a study by IBM, normalized databases can improve query performance by up to 900%.
Don’t Forget about Denormalization
Normalization is great, but it’s not always the best solution. In certain situations, denormalization can actually improve performance. Comparatively, denormalization is the database design process of adding redundant data to a table to improve query performance.
For example, if an application frequently accesses a customer’s purchase history in conjunction with their contact information, it might make sense to denormalize the data and store it in the same table.
Designing for scalability
Scalability is a crucial aspect of database design. As an application grows and receives more traffic, the database must be able to handle the increased load without experiencing a significant drop in performance. There are several strategies that can be used to design for scalability, including:
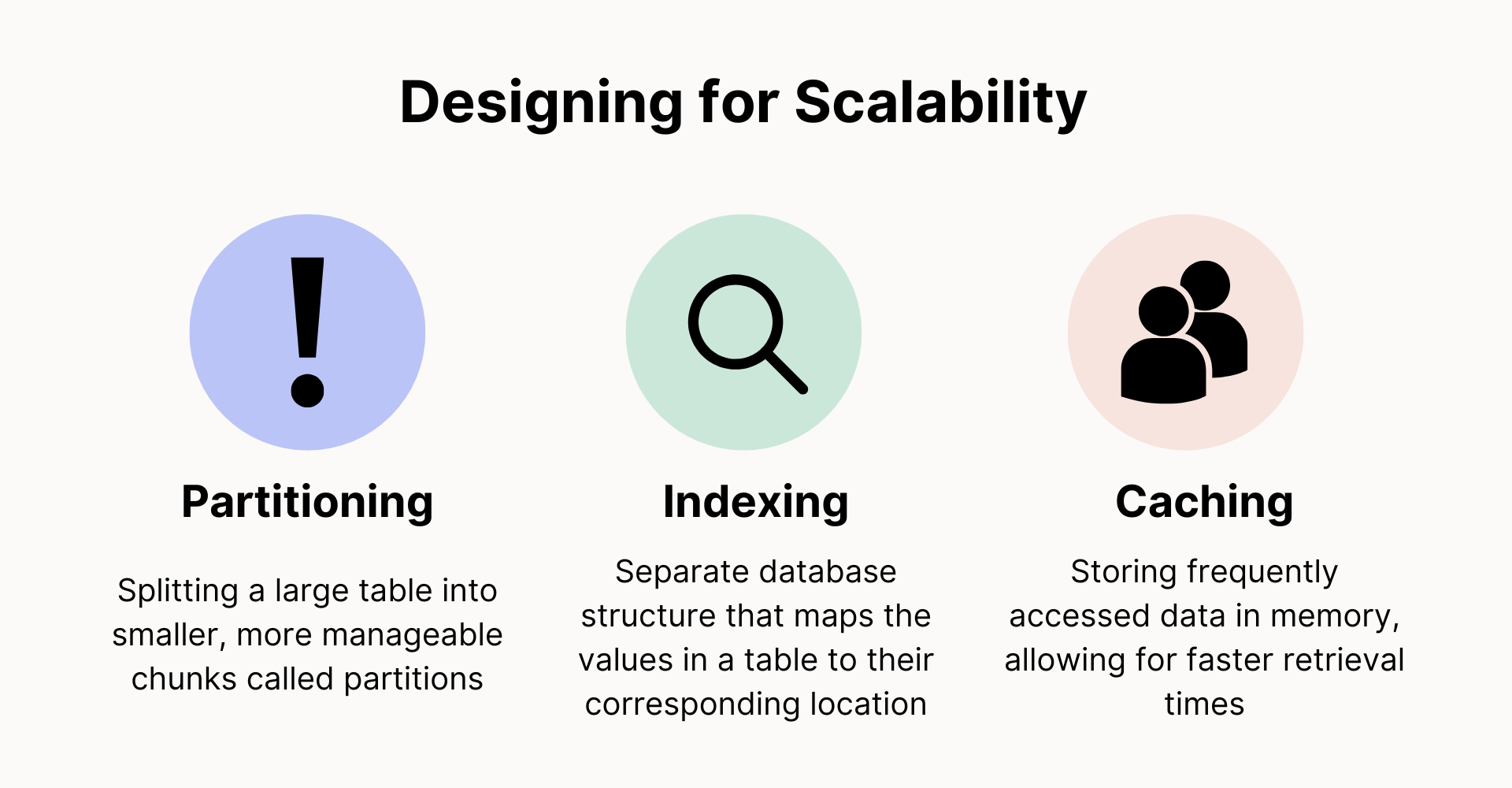
Partitioning:
This involves splitting a large table into smaller, more manageable chunks called partitions. This can improve query performance by reducing the amount of data that needs to be scanned.
Indexing:
Indexing is a technique that can be used to improve query performance. It involves creating a separate database structure that maps the values in a table to their corresponding locations, allowing for faster data retrieval.
Caching:
Caching is a technique that involves storing frequently accessed data in memory, allowing for faster retrieval times.
It’s important to keep scalability in mind when designing a database, as it can greatly impact the long-term success of an application.
Security: Protect Your Information
Database security is also an important aspect of database design. As data breaches become increasingly common, it’s crucial to implement security measures to protect sensitive information. Some strategies for securing a database include:
Encryption:
Encryption is a technique that involves converting data into a format that is unreadable to unauthorized parties. This can be used to protect sensitive information, such as credit card numbers and personal information.
Access control:
Access control is a technique that is used to restrict access to a database based on a user’s role or privileges. This can be used to prevent unauthorized access to sensitive information.
Auditing:
Auditing is a technique that is used to track and log database activity. This can be used to identify and investigate potential security breaches.
By implementing these and other security measures, a developer can ensure that sensitive information is protected and that unauthorized access is prevented.
Firewall:
A firewall is a system that controls access to a network based on predefined security rules. This can be used to block unauthorized access to a database and protect it from potential cyber-attacks.
Applied Database Design: Putting it all Together
Now that we’ve covered the basics of database design, it’s important to put it all together and apply it to your specific application. Here are a few tips for applying database design to your backend development:
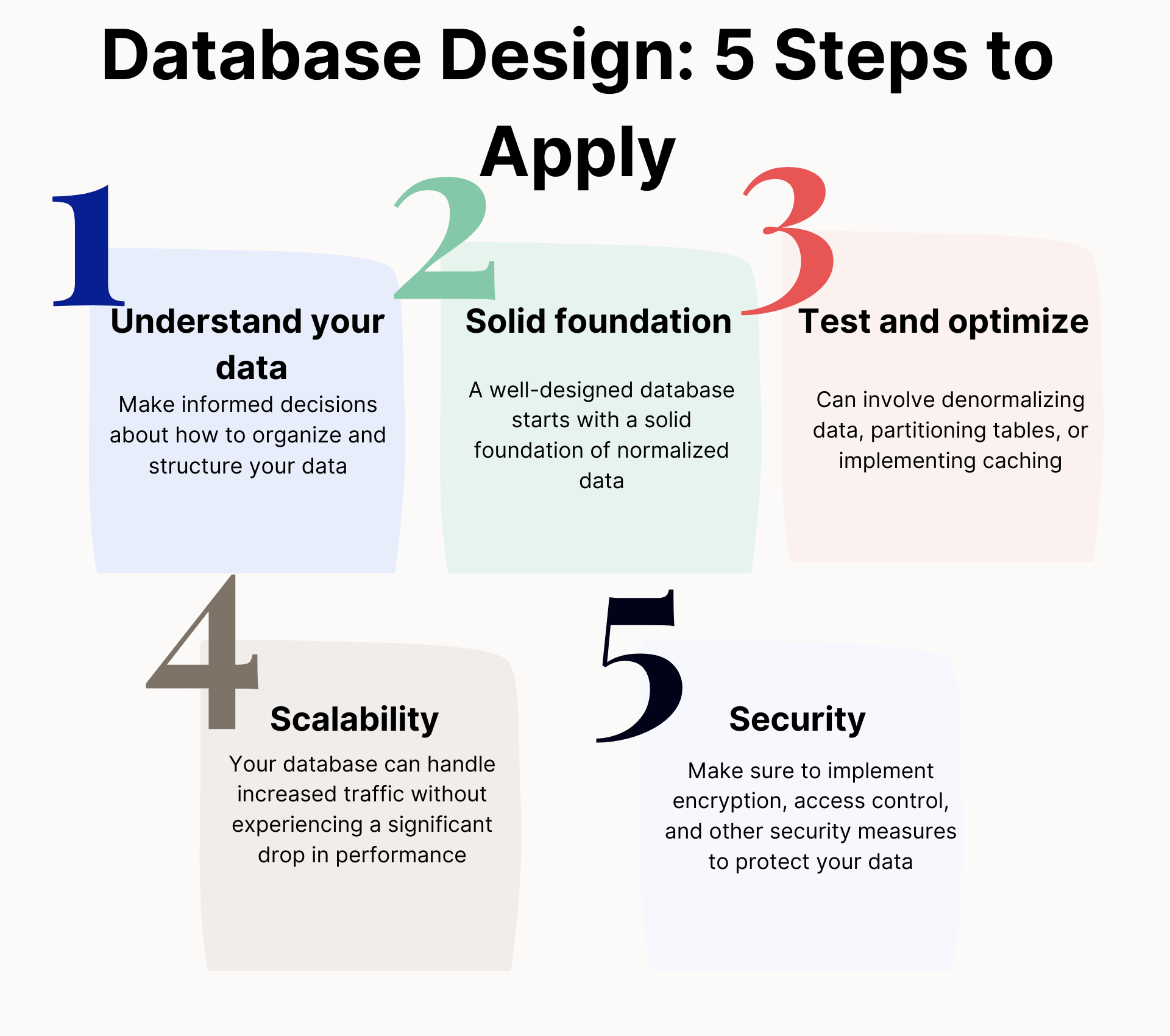
- Understand your data: Before you begin designing your database, it’s important to understand the data you will be storing and how it will be used. This will help you make informed decisions about how to organize and structure your data.
- Start with a solid foundation: A well-designed database starts with a solid foundation of normalized data. This will help ensure that your data is organized, consistent, and easy to query.
- Test and optimize: Once your database is up and running, it’s important to test and optimize it to ensure that it is performing at its best. This may involve denormalizing data, partitioning tables, or implementing caching.
- Keep scalability in mind: As your application grows, it’s important to design your database with scalability in mind. This will help ensure that your database can handle increased traffic without experiencing a significant drop in performance.
- Don’t forget about security: Database security is crucial for protecting sensitive information. Make sure to implement encryption, access control, and other security measures to protect your data.
By following these tips, you can create a well-designed database that will serve as the backbone of your successful application.
With a strong foundation, efficient data retrieval, and built-in security, your application will be able to handle the demands of your users and grow as your business does.
Did you know about this?
Primary keys
Primary keys are a crucial aspect of database design. They are used to uniquely identify each record in a table and ensure data integrity.
A primary key (or a composite key) is a column or set of columns that are used to uniquely identify each record in a table. It must be unique and not null, and it cannot be changed once it is set.
Primary keys are used to link tables together through foreign keys. A foreign key is a column or set of columns in one table that references the primary key of another table.
This creates a relationship between the two tables and allows for data to be queried and joined from multiple tables.
When designing a database, it’s important to choose appropriate primary keys for each table. They should be unique and not nullable, and they should be chosen based on the data and the relationships between tables.
It is also important to consider the scalability of the primary key and the possibility of it running out of space.
In summary, primary keys play a critical role in maintaining data integrity and establishing relationships between tables in a database. They should be chosen carefully and based on the data and relationships within the database model.
Normal forms
Normal form, first normal form, and third normal form are all concepts related to the process of organizing data in a database.
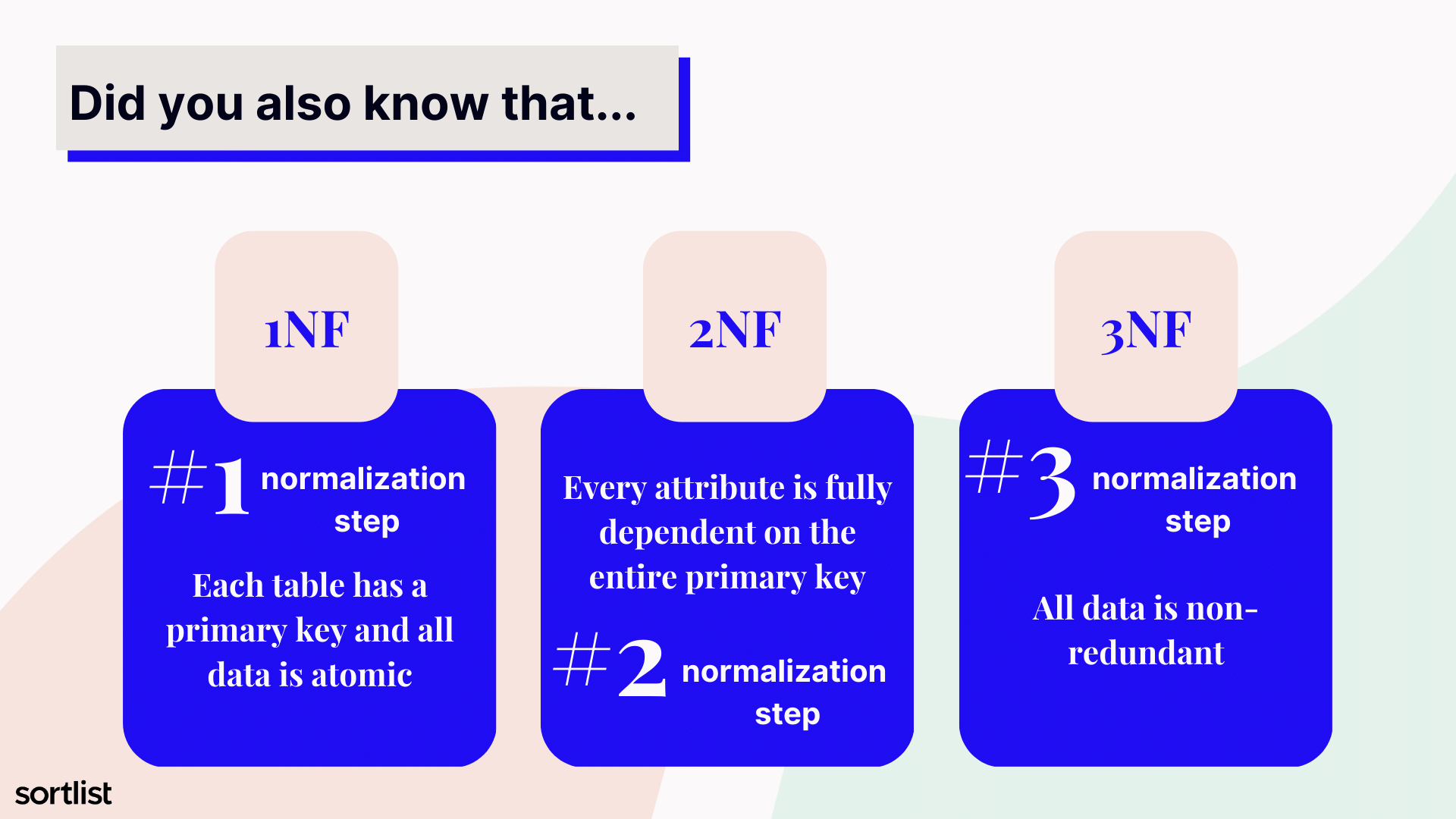
Normalization is the process of organizing data into separate tables to reduce data redundancy and improve data integrity.
The first normal form (1NF) is the first step in the normalization process, and it involves ensuring that each separate table has a primary key and that all data is atomic (cannot be further divided).
The second normal form (2NF) is the second step in the normalization process, and it involves ensuring that every attribute is fully dependent on the entire primary key.
The third normal form (3NF) is the final step in the normalization process and it involves ensuring that all data is non-redundant and that it is only dependent on the primary key.
Conclusion:
In conclusion, database design is a crucial aspect of back-end development. A well-designed database can greatly improve the performance and scalability of an application.
Normalization is an important concept in database design that can help reduce data redundancy and improve data integrity. But it’s not always the best solution. Sometimes, denormalization can help improve performance.
|
Discover the most relevant agencies for your project based on your own specific requirements.
Find an agency!Designing a database is a complex process that requires careful consideration of the specific needs of an application, the expected volume of data, and performance requirements.
It’s important to keep scalability and security in mind when designing a database, as it can greatly impact the long-term success of an application.
With the right design, your application will be able to handle an ever-increasing amount of data and provide a seamless experience for your users while keeping the data safe.
FAQs
The three types of database design are conceptual design, logical design, and physical design.
System design in a database refers to the process of specifying how the database system will be implemented, including defining data structures, relationships, and functionalities to meet the requirements of the intended application.